rename app
This commit is contained in:
@@ -3,18 +3,18 @@ Creating private and secure P2P Docker Managment System
|
|||||||
|
|
||||||
## Introduction
|
## Introduction
|
||||||
|
|
||||||
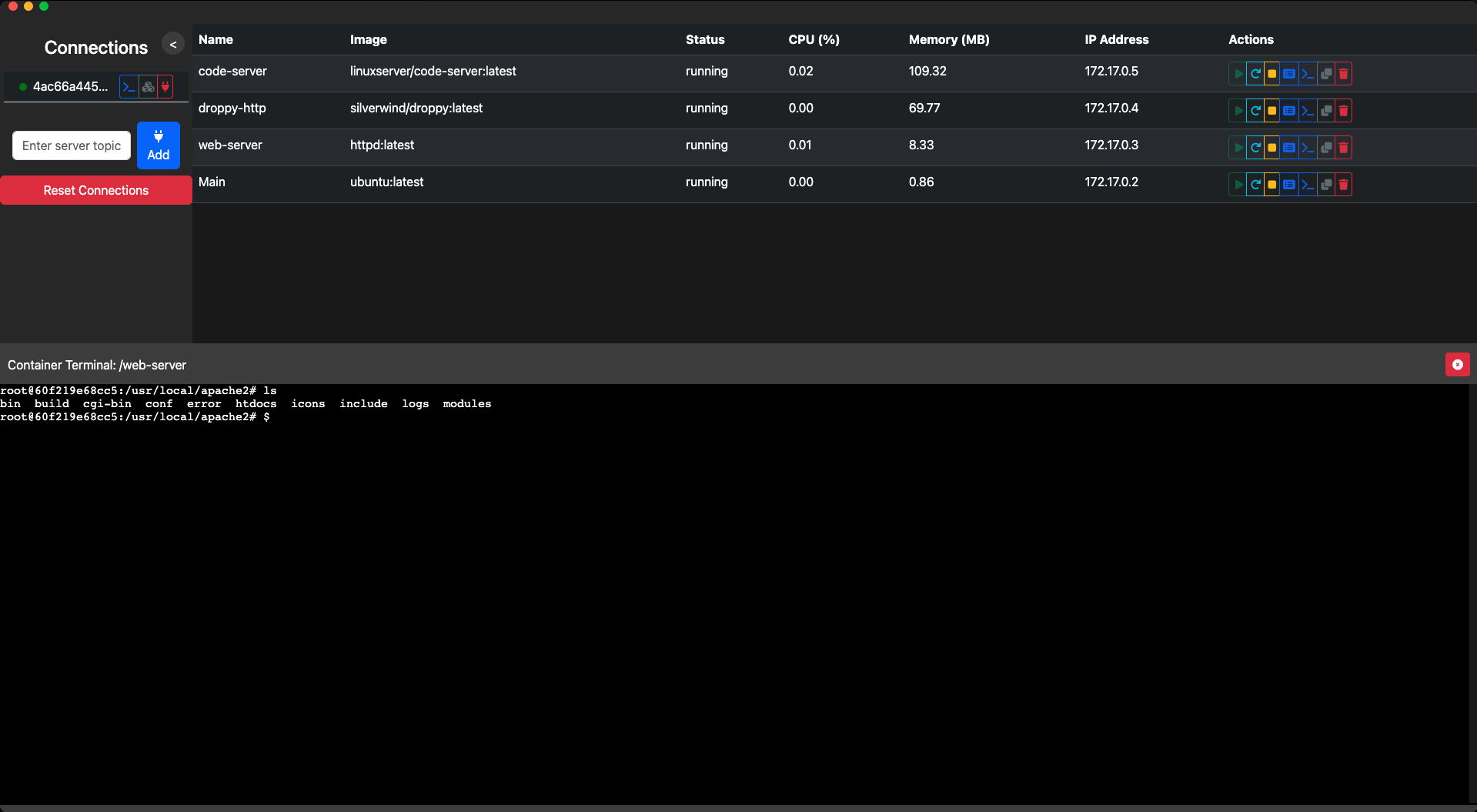
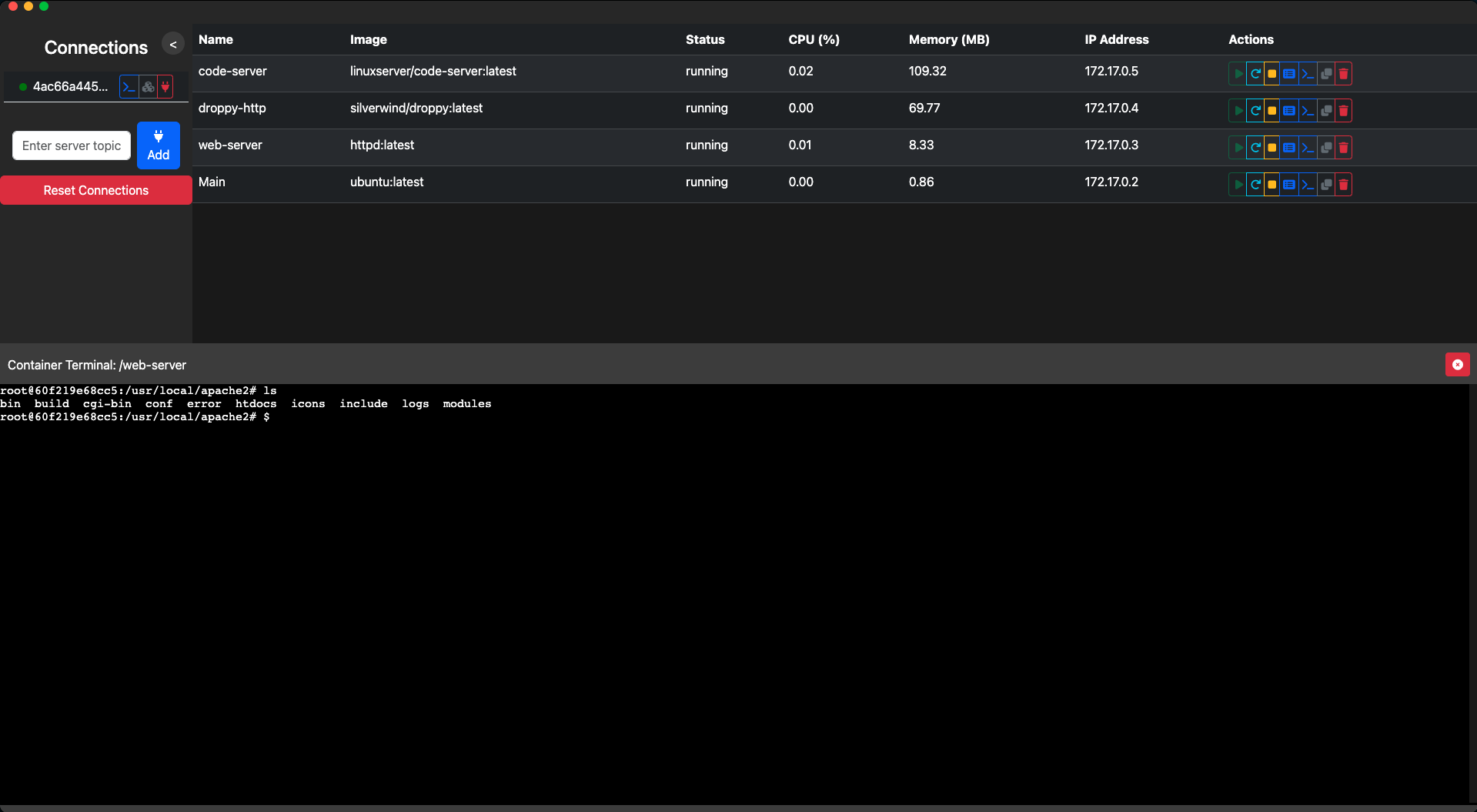
**Peartainer** is an innovative, peer-to-peer Docker management application inspired by [Portainer](https://www.portainer.io/).
|
**Peardock** is an innovative, peer-to-peer Docker management application inspired by [Portainer](https://www.portainer.io/).
|
||||||
|
|
||||||
Portainer offers various options for connecting to Docker environments, including **Agent**, **Socket**, and **REST API Endpoints**, catering to a wide range of use cases. However, deploying Portainer in large networks where exposing management software is a security concern can be challenging. Exposing management interfaces increases the attack surface and may not comply with organizational security policies.
|
Portainer offers various options for connecting to Docker environments, including **Agent**, **Socket**, and **REST API Endpoints**, catering to a wide range of use cases. However, deploying Portainer in large networks where exposing management software is a security concern can be challenging. Exposing management interfaces increases the attack surface and may not comply with organizational security policies.
|
||||||
|
|
||||||
Peartainer addresses these challenges by leveraging peer-to-peer (P2P) networking to securely manage Docker containers without exposing any management software to the network. By using P2P connections, Peartainer ensures that communication between the client and the agent is direct, encrypted, and confined to authenticated peers, enhancing security and efficiency.
|
Peardock addresses these challenges by leveraging peer-to-peer (P2P) networking to securely manage Docker containers without exposing any management software to the network. By using P2P connections, Peardock ensures that communication between the client and the agent is direct, encrypted, and confined to authenticated peers, enhancing security and efficiency.
|
||||||
|
|
||||||
This post provides an in-depth analysis of Peartainer's design, backend architecture, custom message protocol, and the code that powers the entire application.
|
This post provides an in-depth analysis of Peardock's design, backend architecture, custom message protocol, and the code that powers the entire application.
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
# Source: https://git.ssh.surf/snxraven/peartainer
|
# Source: https://git.ssh.surf/snxraven/Peardock
|
||||||
|
|
||||||
## Concept and Motivation
|
## Concept and Motivation
|
||||||
|
|
||||||
@@ -22,14 +22,14 @@ Portainer revolutionized the container industry by providing an easy-to-use inte
|
|||||||
|
|
||||||
However, in large networks where security is paramount, deploying Portainer may not be the most secure option. Exposing management software or APIs can introduce vulnerabilities, and in environments where you do not want to expose any management interfaces, this becomes a critical issue. The risk of unauthorized access, interception, or exploitation increases with exposed endpoints.
|
However, in large networks where security is paramount, deploying Portainer may not be the most secure option. Exposing management software or APIs can introduce vulnerabilities, and in environments where you do not want to expose any management interfaces, this becomes a critical issue. The risk of unauthorized access, interception, or exploitation increases with exposed endpoints.
|
||||||
|
|
||||||
**Peartainer** aims to bring similar functionalities to a peer-to-peer network, eliminating the need to expose any management endpoints. By providing a peer-to-peer client that communicates with its agent solely via a P2P network connection, Peartainer enhances security by:
|
**Peardock** aims to bring similar functionalities to a peer-to-peer network, eliminating the need to expose any management endpoints. By providing a peer-to-peer client that communicates with its agent solely via a P2P network connection, Peardock enhances security by:
|
||||||
|
|
||||||
- **Not Exposing Management Software**: No open ports or endpoints are required, reducing the attack surface.
|
- **Not Exposing Management Software**: No open ports or endpoints are required, reducing the attack surface.
|
||||||
- **Encrypted Communication**: All data transmitted over the P2P network is encrypted using secure protocols.
|
- **Encrypted Communication**: All data transmitted over the P2P network is encrypted using secure protocols.
|
||||||
- **Direct Peer-to-Peer Connections**: Communication occurs directly between authenticated peers without intermediaries.
|
- **Direct Peer-to-Peer Connections**: Communication occurs directly between authenticated peers without intermediaries.
|
||||||
- **Decentralization**: Eliminates the need for centralized servers, mitigating single points of failure and potential targets for attacks.
|
- **Decentralization**: Eliminates the need for centralized servers, mitigating single points of failure and potential targets for attacks.
|
||||||
|
|
||||||
By using peer-to-peer connections, users can manage Docker containers on remote hosts securely and efficiently. Peartainer is designed for environments where security and privacy are critical, such as large enterprise networks, sensitive infrastructures, or situations where network exposure must be minimized.
|
By using peer-to-peer connections, users can manage Docker containers on remote hosts securely and efficiently. Peardock is designed for environments where security and privacy are critical, such as large enterprise networks, sensitive infrastructures, or situations where network exposure must be minimized.
|
||||||
|
|
||||||
## Architecture Overview
|
## Architecture Overview
|
||||||
|
|
||||||
@@ -56,7 +56,7 @@ The backend is a Node.js application that runs on each container host node:
|
|||||||
|
|
||||||
[Hyperswarm](https://docs.pears.com/building-blocks/hyperswarm) is a networking stack that simplifies peer-to-peer connections using distributed hash tables (DHT).
|
[Hyperswarm](https://docs.pears.com/building-blocks/hyperswarm) is a networking stack that simplifies peer-to-peer connections using distributed hash tables (DHT).
|
||||||
|
|
||||||
In Peartainer:
|
In Peardock:
|
||||||
|
|
||||||
- Each peer joins a swarm identified by a unique **topic** (a cryptographic key).
|
- Each peer joins a swarm identified by a unique **topic** (a cryptographic key).
|
||||||
- Peers discover each other by announcing and looking up this topic in the DHT.
|
- Peers discover each other by announcing and looking up this topic in the DHT.
|
||||||
@@ -78,14 +78,14 @@ It allows:
|
|||||||
- Executing commands inside containers.
|
- Executing commands inside containers.
|
||||||
- Streaming logs and stats.
|
- Streaming logs and stats.
|
||||||
|
|
||||||
In Peartainer's backend (`server.js`):
|
In Peardock's backend (`server.js`):
|
||||||
|
|
||||||
- Dockerode interfaces with the local Docker daemon.
|
- Dockerode interfaces with the local Docker daemon.
|
||||||
- Commands received from peers are executed, and responses are sent back securely.
|
- Commands received from peers are executed, and responses are sent back securely.
|
||||||
|
|
||||||
## Custom Message Protocol
|
## Custom Message Protocol
|
||||||
|
|
||||||
Peartainer uses a JSON-based custom message protocol over Hyperswarm connections.
|
Peardock uses a JSON-based custom message protocol over Hyperswarm connections.
|
||||||
|
|
||||||
### Command Structure
|
### Command Structure
|
||||||
|
|
||||||
@@ -362,7 +362,7 @@ case 'deployContainer':
|
|||||||
|
|
||||||
## Final Thoughts
|
## Final Thoughts
|
||||||
|
|
||||||
Peartainer brings a novel approach to Docker container management by harnessing peer-to-peer networks. By eliminating the need to expose any management software or endpoints, it offers a secure, decentralized, and efficient way to manage containers across different hosts.
|
Peardock brings a novel approach to Docker container management by harnessing peer-to-peer networks. By eliminating the need to expose any management software or endpoints, it offers a secure, decentralized, and efficient way to manage containers across different hosts.
|
||||||
|
|
||||||
The combination of Hyperswarm for networking and Dockerode for container management provides a robust backend. The custom message protocol ensures structured and efficient communication between peers, confined to authenticated connections.
|
The combination of Hyperswarm for networking and Dockerode for container management provides a robust backend. The custom message protocol ensures structured and efficient communication between peers, confined to authenticated connections.
|
||||||
|
|
||||||
@@ -375,4 +375,4 @@ The frontend offers a user-friendly interface with advanced functionalities like
|
|||||||
- **Plugin System**: Allowing third-party plugins to extend functionalities and adapt to specific needs.
|
- **Plugin System**: Allowing third-party plugins to extend functionalities and adapt to specific needs.
|
||||||
- **Mobile Support**: Optimizing the UI for mobile devices to manage containers on the go.
|
- **Mobile Support**: Optimizing the UI for mobile devices to manage containers on the go.
|
||||||
|
|
||||||
Peartainer is a testament to the possibilities of decentralized applications and opens new avenues for managing containerized applications in distributed and security-sensitive environments. It combines the best of Portainer's user experience with the security and privacy benefits of peer-to-peer networking.
|
Peardock is a testament to the possibilities of decentralized applications and opens new avenues for managing containerized applications in distributed and security-sensitive environments. It combines the best of Portainer's user experience with the security and privacy benefits of peer-to-peer networking.
|
||||||
Reference in New Issue
Block a user